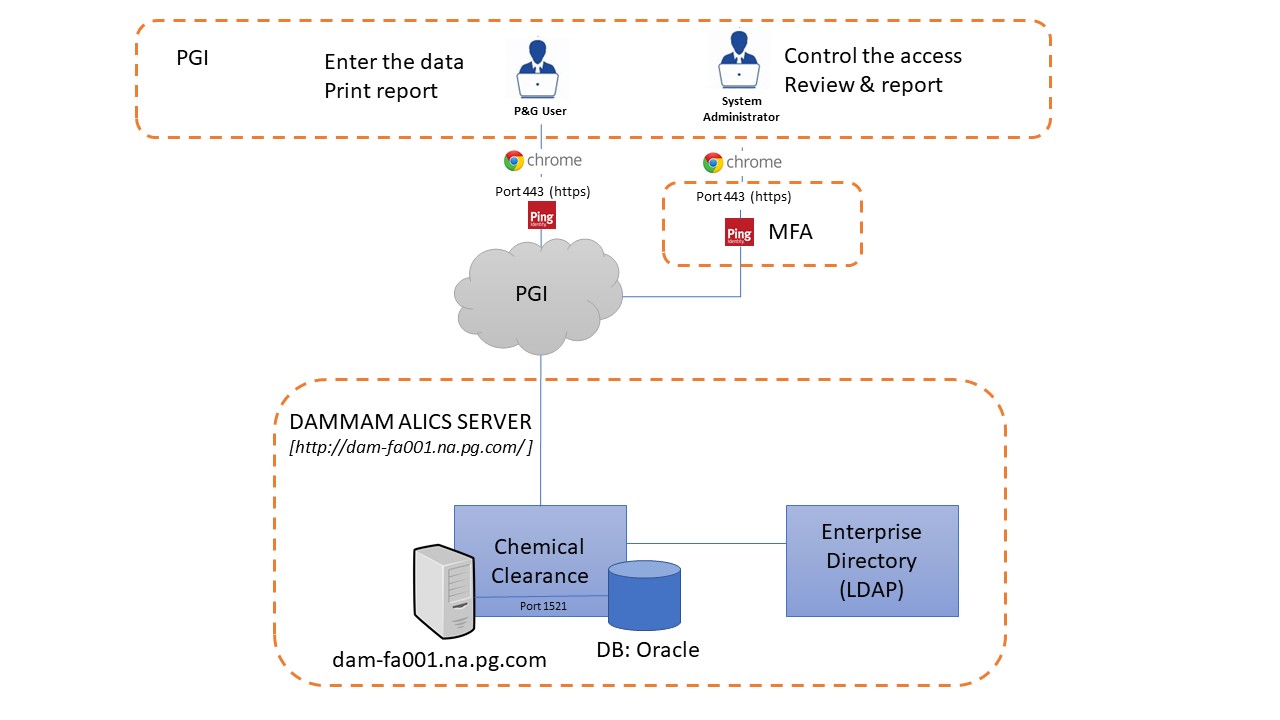
WHO is involved: You should be able to easily see the Users, Administrators, and other applications involved. They should be identified by the Role. They should also be identifiable as employee or non-employee WHAT information is exchanged: This should include the information exchanged between users and other applications You should be able to understand the format/method that is being used to exchange the data HOW are users and systems authenticated: As a general rule, avoid using acronyms on the diagrams. Applications should be identified by the Application ID or HexID, found on General information tab under Others, along with the Name of the application IN OTHER WORDS “If your mother looked at the diagram, would she know what this is doing?
--


